In one of the previous articles, we showed you how to use filters to exclude spam in Google Analytics. This solution was quite good, however, the spammers get better and we have to use a better technique to fight them back.
In one of the previous articles, we showed you how to use filters to exclude spam in Google Analytics. This solution was quite good, however, the spammers get better and we have to use a better technique to fight them back.
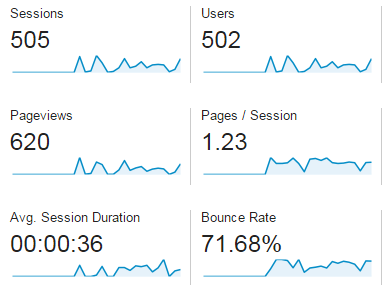
The issue with the fake traffic (also called ghost traffic) is that it completely spoils your analytical data. On top of that, the spammers often fake more pages visitied and non-zero average time on the page. (more…)
 Leading smartphone manufacturer Apple is expected to unveil the upgraded avatar of its iPhone 6 by the end of 2015. Projected as iPhone 6s, the new smartphone will be bringing is some serious upgrades over its predecessor. Usually, Apple’s “S” models don’t feature big upgrades compared to their counterparts, but this time around, the new phone is expected to come with some crucial improvements and new features.
Leading smartphone manufacturer Apple is expected to unveil the upgraded avatar of its iPhone 6 by the end of 2015. Projected as iPhone 6s, the new smartphone will be bringing is some serious upgrades over its predecessor. Usually, Apple’s “S” models don’t feature big upgrades compared to their counterparts, but this time around, the new phone is expected to come with some crucial improvements and new features.

 Reliability is the ruling factor that drives the choice of an appropriate communication technology for any organization. For instance, when we consider the case of SIP trunking, majority of the companies would not like to completely abandon the older technologies like TDM (Time-Division Multiplexing) or PSTN (public switched telephone network). SIP trunking offers a more cost effective and efficient alternative to the aforementioned traditional technologies; however companies are still reluctant because they are not sure about the quality of the calls and the performance of the technology during an emergency.
Reliability is the ruling factor that drives the choice of an appropriate communication technology for any organization. For instance, when we consider the case of SIP trunking, majority of the companies would not like to completely abandon the older technologies like TDM (Time-Division Multiplexing) or PSTN (public switched telephone network). SIP trunking offers a more cost effective and efficient alternative to the aforementioned traditional technologies; however companies are still reluctant because they are not sure about the quality of the calls and the performance of the technology during an emergency.